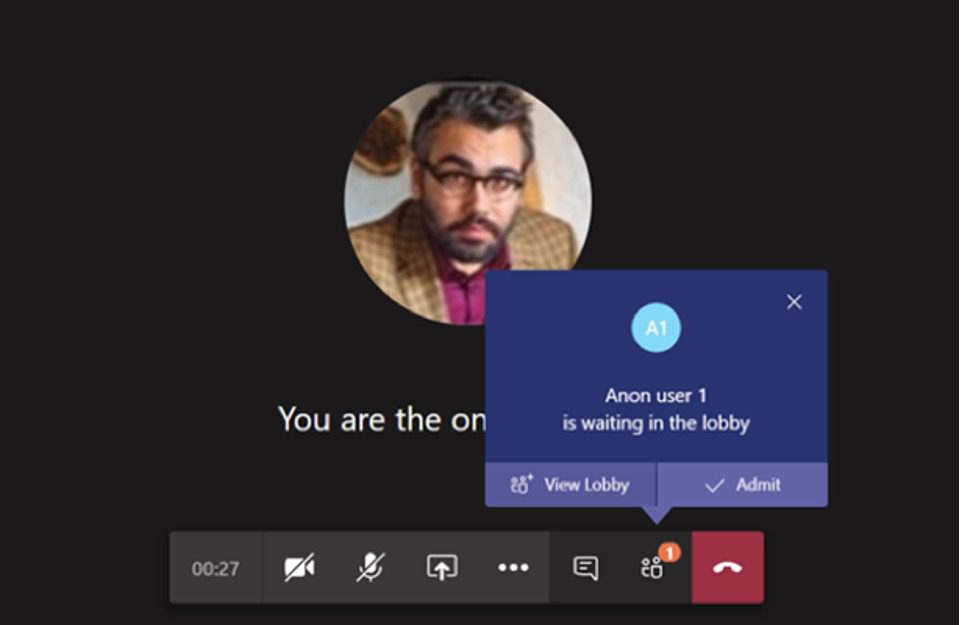
With the continued use of Microsoft Teams to conduct virtual meetings, it’s important to know how to protect your company’s privacy.
When you rely on Microsoft Teams to conduct virtual meetings, it’s important to implement tactical best practices to protect your organization’s privacy from intruders.
Even while several organizations head back to the office following years of remote work due to the pandemic, there is still a significant percentage of employees either working from home full-time or within a hybrid work model. As a result, virtual meetings aren’t going away any time soon. And while there are many pros to this type of collaboration, there are also some risks to address.
As we know, virtual meetings have many positive outcomes, such as allowing companies to continue operations to support their workforce and customers, schools from kindergarten through college to provide classes, and families to schedule meetups for virtual dinners and conversations.
Unfortunately, the great popularity of platforms like Zoom also increased the number of hackers and trolls out to create their versions of “fun, violating the privacy of the meetings’ topic and discussion. The problem is so common and growing so quickly that the FBI invented a term for it: Zoom-bombing.
The Privacy and Security Risks of Virtual Meetings
Sometimes, you get merely annoying interruptions, but other times, hackers can cause real problems. After all, even when intrusions seem harmless, they can open more considerable security risks. For example:
- In the Bay Area, CA, Zoom bombers broke into several City Council meetings to shout antisemitic comments and racial slurs.
- A recently discovered flaw in Zoom and AudioCodes products points to the ability for potential hackers to “listen in on video conferencing calls, hijack vulnerable endpoints,” and more.
- Similarly, hackers might now be able to steal passwords over Zoom using AI, with up to 93 percent accuracy.
Although these examples all relate to Zoom, other platforms are vulnerable, too, including Teams. In fact, hackers and trolls can break into any platform that isn’t properly configured, doesn’t have sufficient security in place, or is operated by meeting organizers who didn’t take steps to run their meetings in a secure and controlled manner.
Breaking into a Teams meeting and violating your organization’s privacy doesn’t even require much technical skill on the part of a hacker. Consider this common scenario that happens all the time:
- A meeting organizer creates a meeting in which anyone with the link can join.
- Someone in the company mistakenly forwards the link to someone who doesn’t belong on the call.
- A bored teenager picks it up off of an employee’s laptop when they step away from their home office and then distributes the dial-in number.
As you can see in this scenario, anyone can do it. So, how can you stop it?
Protect the Privacy of Microsoft Teams Meetings
The good news is Teams offers easy ways to mitigate the risk of such privacy problems by updating your settings.
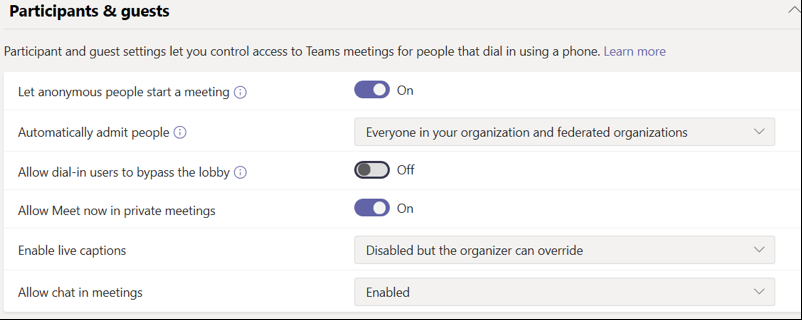
In the Teams admin center, you can make the following simple changes to lock down who you allow into meetings:
- Change “Automatically admit people” to “Everyone in your organization and federated organizations.”
- Turn off “Allow dial-in users to bypass the lobby.”
Here is what it looks like on the Teams Admin Center interface:
https://techcommunity.microsoft.com/t5/microsoft-teams/can-t-get-the-devices-details-teams-admin-center-teams-devices/m-p/3696273
https://techcommunity.microsoft.com/t5/microsoft-teams/teams-meeting-policy-quot-allow-everyone-quot-not-working/m-p/1458665
NOTE: The first setting, “Let anonymous people start a meeting,” should be “On” if many people in your organization need to start meetings through dial-in (i.e., when they aren’t able to start the meeting through the Teams interface).
These changes will allow your Teams users to admit non-organizational guests from the lobby into the meeting manually. However, you must admit people into the meeting from within the Teams app itself, not through the dial-in connection to a Teams meeting.
As always, we strongly recommend you communicate these changes clearly to your users so they know the “why” behind the change, which will reduce frustration and increase adoption.
Embrace Remote Meetings Without Sacrificing Confidentiality
You can complete the steps I outlined in this post in seconds and eliminate a lot of headaches. By learning the Rules of the Road for Microsoft Teams, you can make sure you configure your Teams tenant properly and make your Teams security even tighter.
As your use of remote teleworking applications continues to increase, you always need to consider how you configure these applications to ensure the security and privacy of your information, discussions and meetings. That way, we can all get better and do better together.