When you need to move fast or hiring in-house isn’t an option, investing in Virtual CISO consulting services can enable you to quickly pivot to meet required compliance demands and stay on top of your organization’s cybersecurity.
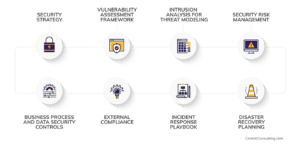
Addressing best practice security initiatives requires serious time from executives. The list is long; risk and compliance management, threat monitoring, intelligence, incident response and recovery plans, to name but a few. Given the prevalence of threats, none of these are optional.
Our seasoned Virtual CISO Services team can define and lead these initiatives for your organization, resulting in a comprehensive approach to cybersecurity that includes on-demand CISO services, governance, prevention, detection, response and program development.
Whether you need a complete IT security strategy, improved metrics to drive your security maturity, or a service-based security resource, our full-time or fractional Virtual CISO experts are here to help.