IT risk is not a thrilling type of uncertainty. And risk gone wrong is disastrous. Here are three steps to analyze and manage your company’s IT risk.
For most people, risk is a part of life. Sometimes taking risks can even yield big rewards, whether it’s buying a new stock or deciding to change jobs to pursue your dreams.
But for those of us who work in IT, taking risks rarely yields rewards. In fact, it can be disastrous. Consider security breaches that expose customers’ private information, or data loss that cripples your processes, or hardware failures that bring your factory floor to a standstill. Application failures can cause frustration at best, and massive financial losses at worst.
The good news is, you can manage IT risk—but first, you have to understand various risk factors: the kinds of risk you face, how likely each is to occur, the impact of each, how quickly it could happen, and how long it might take to recover.
Conducting this analysis is a simple, three-step process:
- Talk to your people. The subject matter experts (SMEs) who work with your systems every day best understand the scope of the risks you face.
- Quantify the risk. A simple scoring system helps to weigh what’s at stake with each potential risk.
- Put your data to work. With each risk quantified, you can make smart decisions about how to eliminate risks, develop strategies for handling impacts if problems occur, and how to monitor risks as systems change.
Step 1: Talk to Your People
Chances are, when you ask your SMEs to evaluate risk, they won’t know where to begin. Help them out by providing a set of questions to help contextualize risk, such as:
- What is the most likely risk you face every day?
- What would be the most difficult risk to recover from, in terms of technical resources needed?
- What would be the most costly risk to recover from, in terms of dollars, time or resources?
- What risk presents the most threat to your company’s reputation?
- What risks are completely out of your control, like floods or earthquakes?
- What risks must you mitigate due to regulatory requirements?
Step 2: Quantify the Risk
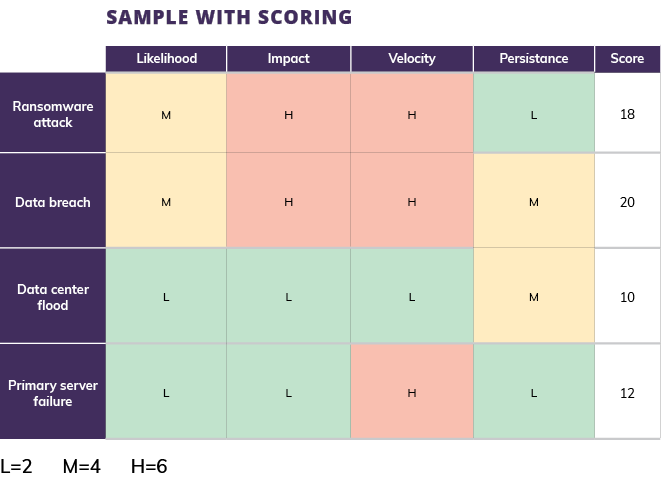
With the various risks listed, assign point values for each based on measures such as Likelihood, Impact, Velocity and Persistence. In the example grid below, measures ranked “low,” equal two points, “medium,” four points and “high,” six points. Simply add the points together to identify the greatest risks.
Step 3: Put Your Data to Work
Continuing with this example, it’s clear that defending against a data breach is the top priority. Building a floodwall? Not so much. But that doesn’t mean you shouldn’t be prepared for that risk—it just means it’s a lower priority as your start to implement your risk-management assessment.
Obviously, your goal is to eliminate as many risks as possible. But let’s be honest, life happens. So, part of your assessment should include deciding how to evaluate impact if worse comes to worse. The scale might look something like this:
- Reduce Impact: Take proactive measures to be as prepared as possible. For example, implement training programs so employees know what to do if a certain disaster strikes.
- Avoid Impact: Adjust your business practices to avoid the impact of risk. Scheduling a major upgrade over a weekend when volume is down is a common way companies avoid impact.
- Transfer Impact: Craft contracts to transfer the cost of risk to other parties, like third-party suppliers.
- Share Impact: Plan for multiple groups in your organization to share risk impact so one department isn’t completely affected. For example, you might have plans to bring resources in from other areas.
- Accept Impact: Use your LIVP score to identify risks that are so unlikely, or have such small impacts, that the cost of preventing them is not something the cost of recovery should cover.
Finally
Because the only thing as constant in life as risk is change, make sure you periodically repeat this process—say, once a quarter—to make sure that you are taking shifting risks and business priorities into account.