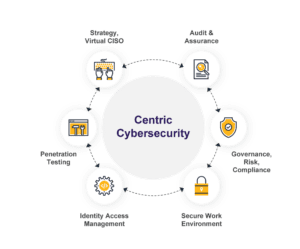
How Consulting & Penetration Testing Services Work at Centric
Our consulting and penetration testing services ensure that you’re prepared for new threats, and able to save resources otherwise spent on remediating expensive breaches. You’ll get peace of mind that comes from knowing your security posture has been rigorously tested.
By performing regular penetration testing, you achieve cyber liability compliance, a clean bill of health for an application launch, a secure attestation post-critical firewall and network system changes, and compliance with security frameworks.
Our Approach to Penetration Testing
We take a risk-based approach to scoping penetration testing engagements. This allows us to focus on your highest risk assets while reducing unnecessary costs. Using industry metrics for benchmarking and root cause analysis, we generate illuminating reports that are detailed and actionable while also being easy to understand.
The Phases of Our Penetration Testing Process
As a seasoned cybersecurity consultancy, we create and document a multi-phase pen-testing approach that meticulously analyzes and synthesizes information into prioritized remediation plans. This approach has 5 distinct steps:
1. Planning & Project Scoping – establish the scope, rules of engagement, timeline and type of pen testing required.
2. Reconnaissance – gather information about target networks and systems including public information, information obtained via social engineering, foot-printing, port scans and more.
3. Vulnerability Discovery – use a host of manual and automated techniques to identify high risk vulnerabilities and misconfigurations in target networks and systems.
4. Exploitation – attempt to gain access to target systems and networks.
5. Reporting – detail vulnerabilities, remediation recommendations and a roadmap for hardening of systems.
Our Process for Assessing Your Penetration Testing Requirements
When our pen testers assess your unique testing requirements, the first step is to establish the planning and project approach. This involves defining the assessment’s scope, which outlines the systems, applications or infrastructure components we’ll evaluate. We’ll work with you to establish rules of engagement which set the guidelines needed to ensure legal and ethical compliance.
Using a tailored combination of manual and automated techniques, our experts then discover high-risk vulnerabilities and misconfigurations in the target environment. We exploit these weaknesses, attempting to gain access to systems and networks.
Finally, we provide a comprehensive pen testing report detailing vulnerabilities identified, along with actionable remediation advice and a roadmap for hardening your defenses. This structured approach ensures a thorough, systematic evaluation and leveling up of your security posture.
We Customize Penetration Testing Based on Your Business Needs
Our penetration test services are unique — there’s no one-size-fits-all solution. We work closely with your team to identify critical assets, prioritize testing areas and methodologies, and develop customized test cases that align with your business objectives and risk appetite.
This level of customization allows us to provide you with actionable insights and recommendations that directly address your organization’s vulnerabilities and mitigate your security risks while empowering you to make informed decisions to fortify your security posture.