Learn about digital asset protection in Microsoft 365, from encryption and legal compliance to identity control, physical architecture, and more, in this blog.
Security is a broad topic, but the goal is the same. Most of us just want to know answers to questions like: Do we have security? Is there enough security? Should we improve our security? Security in conjunction with technology, such as in the sense of digital asset protection, used to be a scary topic, somewhat inaccessible, and best reserved for “nerds” and cyber sleuths.
Now, it’s critical.
Why Asset Protection Is Important
Encryption for Microsoft 365 Cloud Security
Microsoft 365 for Legal Compliance
A New Strategy for Identity Control
Security Policies in Microsoft 365
Physical Architecture: Security Features
Business Continuity and Disaster Recovery in Microsoft 365
Additional Business Continuity Tips
Operational Support Structure for Digital Asset Protection
Digital Asset Protection in Microsoft 365: Final Thoughts
Why Digital Asset Protection Is Important
While working as a consultant at a global manufacturer in the 1990s, I first heard the phrase, “Security is everybody’s business.” This company had, and likely still has, a robust security training program with videos, classes and more.
I admit that I scoffed at this effort until I first flew somewhere for business. Across the aisle and one row up, a well-dressed man extracted a laptop and shared his company’s financial information with all of us behind him. Then, I understood.
We’ve come a long way since then, yet I still get questioned today about why I use complex passwords and two-factor authentication for everything. My answer: Some service passwords in Azure require 12 characters, and I will always recommend multifactor authentication.
With everything in the cloud, security is now more important than ever especially when it comes to protecting your two biggest assets: identity and information.
This blog will focus on both identity and information – from the tools available to how they work together to achieve a holistic and security-centric approach to your cloud investment in Microsoft 365 and Azure. I’ll specifically dive into seven areas to keep in mind to thoroughly protect your digital assets.
While the focus won’t be on the technical procedures for implementing these tools, rest assured that I’ll direct you to the technical references everywhere possible.
1. Encryption for Microsoft 365 Cloud Security
Vigenère. Playfair. Enigma. Sha. MD5. RSA. AES. Perhaps you have heard of these ciphers, especially the later ones like RSA and AES. Today, RSA and AES are the safest, but with every advance in computing power comes the need to update this cipher technology. With the rapidly approaching era of available DNA and Quantum computing, we’ll soon be able to easily decode the final Enigma and Zodiac ciphertexts that have remained uncracked for years.
RSA is the cipher used for today’s public key cryptography implementation and is the public key infrastructure widely in use. To securely facilitate the transfer of information, a message sender uses a known public key to encode a message, and the recipient uses a private key, known only to them, to decode the message. Handshakes and agreements between sender and receiver ensure the quality of the encoding or decoding.
You can use these encryption technologies to protect assets in your Microsoft 365 platform and Azure. Here’s how:
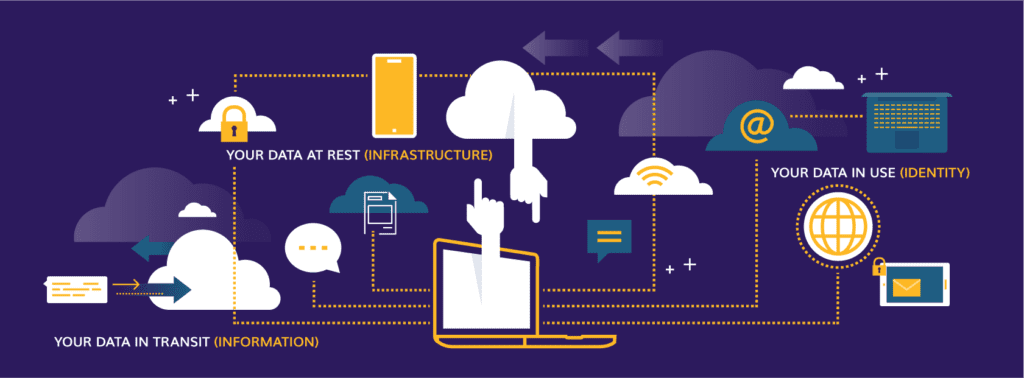
Your Data at Rest (Infrastructure)
When it is not being sent, received or used, your organization’s data lives on a server in a datacenter.
Your data is replicated for security and high availability, but while it is at rest in any Microsoft facility, it resides on a storage mechanism encrypted using Bitlocker.
Be sure to gather information in the links above to reference the location of your organization’s data. This is extremely important for topics like the General Data Protection Regulation (GDPR) in the EU and High Availability, which describes a system’s ability to continue operating even when some components of that system fail.
Your Data in Transit (Information)
Your data in transit is the most customer-involved decision-making piece of the Microsoft 365 encryption solution. That is why we work so hard to provide updated guidance and support throughout the life of your Microsoft 365 investment.
Dozens upon dozens of endpoints are available from any device and any location in the world, providing information entrance and exit paths to and from the various services Microsoft 365 and Azure offer.
Protecting the information flowing through these points is critical, especially since users are historically unreliable when it comes to classifying and encrypting messages and files on their own.
At the application layer (OSI 7), Microsoft provides Transport Layer Security and Secure Sockets Layer (TLS/SSL) (currently version 1.2) encryption, the successor to SSL and a means of negotiating a handshake between sender and receiver to generate agreed-upon keys to encrypt data being sent – this is also known as symmetric cryptography.
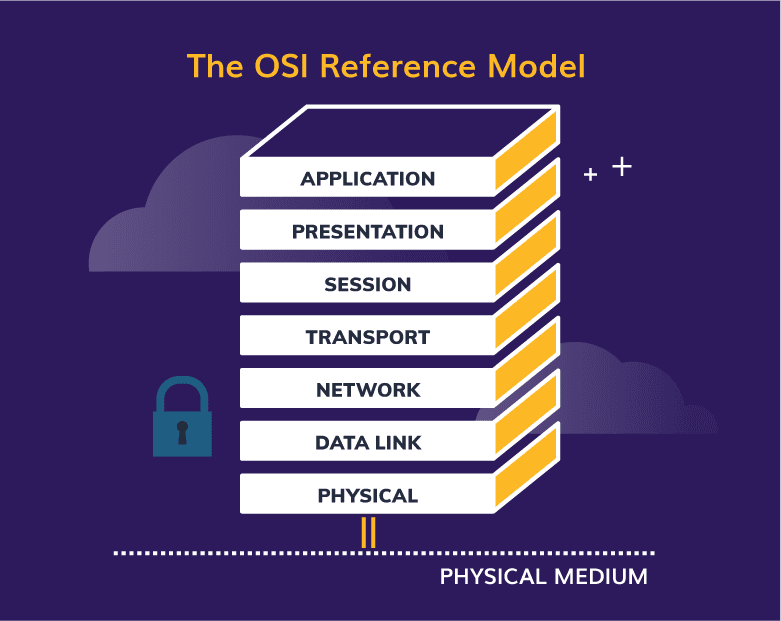
Original image: https://learn.microsoft.com/en-us/windows-hardware/drivers/network/windows-network-architecture-and-the-osi-model
The sender and recipient must agree on the encryption method based on what is available to them and what is in common between them. As a result, this does not always guarantee the highest level of security, but it does guarantee the highest level of security in common between both parties.
Here are some of the customer tasks involved with data-encryption information security:
- Avoid accidental and malicious data deletion by configuring:
- Data Loss Prevention (DLP) and Labels in Microsoft Purview – This is not encryption-related, but important nonetheless.
- Avoid accidental and malicious data exfiltration using:
- Azure Rights Management Service (RMS) – Applies protection and encryption to messages and data.
- Information Rights Management (IRM) – Applies protection and classification to messages and SharePoint libraries.
- Microsoft Purview Information Protection (IP) – Applies classification, encryption, and permissions for use through policies for data and messages.
- Exchange Online Protection (EOP) along with other Exchange settings – Strengthens your basic messaging stance with rules and malware policies, to name a few.
- Avoid accidental and malicious data contamination using:
- Microsoft Defender for Office 365 – Send messages through an isolated channel to a detonation chamber to thoroughly test any message links and attachments, and remove them where necessary. Also, it is not specifically encryption-related, but it is important nonetheless.
Your Data in Use (Identity)
When you and your colleagues collaborate on a document using Microsoft Teams, the source document resides in SharePoint by default. Whether it is OneNote, OneDrive, or a SharePoint document repository opened in Teams, Office Online, or a client, you can encrypt all communications between the client and the data source using Azure VPN Gateway.
If you have configured and deployed the information encryption options previously mentioned, these will also be in use during the collaborative transport of data.
If, or when, you receive an encrypted email, your identity is verified, and permissions for the message and its attachments are maintained using IP in concert with Azure RMS. This information is only visible with a protected viewer (client or browser) and is otherwise encrypted at all times.
Users can set the encryption, or it can be done automatically using various criteria set in the IP control panel. My colleague Veenus Maximiuk does a much more thorough job of explaining this in her blogs, so I’ll leave the details to her.
Your organization’s discussions around each encryption technology mentioned above will depend on what features of Enterprise Mobility + Security (EMS) you’re going to deploy and what hybrid design elements are in place. The solution will not be single-sized and will differ, sometimes drastically, between organizations.
One major factor to consider while determining which features are best for your digital asset protection needs is the legal regulations that impact your organization.
2. Microsoft 365 for Legal Compliance
The tools you need for security and legal compliance, transparency, and reporting are in the Microsoft Purview compliance portal and various other Microsoft sites specific to these topics. This compliance portal is the hub for legal work and protects your data using specific user roles for different operations in the center.
Microsoft maintains a high level of transparency, trust and certifications surrounding the services it offers in the cloud, and you can locate any information your legal department requires using the above links.
Digital asset protection plays a major role in both security and compliance. There was no shortage of security incidents in 2023, and all of them had legal implications in some measure.
For example, I was fortunate enough to be able to provide guidance and technical assistance in an incident involving a Microsoft 365 user in a foreign country who was involved in a legal investigation.
The legal team requested that an email be held, which is as simple as a checkbox and a duration option. However, they were unaware that there were also options for locating and holding data in place in other locations, such as Groups, Teams, SharePoint, and OneDrive.
For this particular incident, we used an eDiscovery case to perform all the required holds, content searches, and exports. An eDiscovery case allows us to create a case, assign users, search for content, select locations where we want to search, retain that data, report on it, and finally export it for transport.
I only encountered a few issues at the time, and the main one was the time frame. I didn’t know anything about the case – and I like to keep it that way – but we had 72 hours to make usable data available to the legal team in the other country.
With about 150Gb in the mailbox, it was slow – Microsoft has made improvements to increase the speed of operations, and it is much faster now – and had to be split into multiple files.
One thing we know for sure when trying to find what you need: Narrow down those searches using filters and locations to get exactly what you’re looking for for your case! You will save time, reduce throughput issues like timeouts, create more space, and probably some more time.
Security and Compliance Center Capabilities
So, what do you need, and what are your capabilities in the Microsoft Purview compliance portal?
First, you’ll need a Microsoft 365 Enterprise E3 license or a la carte P2 licenses for Exchange and SharePoint to retain user data. Also, if you need enhanced security and management, you’ll need an EMS license to use Microsoft Purview IP, as well as advanced features of MFA, and more.
Next, use the following tools as needed within your organization:
- Classification labels and DLP policies – To retain, detect or delete particular information for a period of time. The GDPR Dashboard brings these tools together quite nicely as well.
- Content Search – To find the information you need, based on the criteria you have, in the locations you select, and for the individual who creates and uses it.
- Audit Log – To search for and locate any administrative activities for an individual or by a particular administrator.
- eDiscovery – Serves as a complete management tool for legal cases, including searching, holding, exporting, and reporting on user data. I’ve also used the eDiscovery tool in the past to retain departed employees’ information for a required period of time.
There are plenty of tools available for this and, with the use of archive mailboxes and other strategies, plenty of storage available for these operations.
It is important to remember that once you put a user’s data location on hold, that data and any data generated by the user from that point forward will be retained. I have yet to see any organization deplete their tenant space entirely, much less with eDiscovery as the reason (and I’ve seen some really large operations using a lot of space).
But in order to do anything with a specific user’s data location or other information, you need to make sure your company has a strategy for identity control.
3. A New Strategy for Identity Control
Prior to transforming your business to meet today’s needs, you probably created an account for your user in your company’s directory.
You likely provided that account with permissions to folders and applications on your network – perhaps individually or in groups. And, you fully understand where your users will be logging in, from what devices, and at what times.
But with today’s business anywhere mentality, you can no longer protect your digital assets and users’ identities using the old methodologies for on-premises networks. And if your company isn’t ready or cannot be completely in the cloud, then you’ll need a hybrid strategy.
Steps to Identity Control in a Hybrid Environment
Enter Azure role-based access control (RBAC), Microsoft Entra Privileged Identity Management (PIM), Microsoft Entra ID Protection, and the Microsoft Graph Security API based on machine learning and AI.
When you make a move to a hybrid cloud scenario you will need these. You will also want Microsoft Intune for device management, which is the other side of the identity control scenario.
The hybrid strategy will remain until all your existing software solutions – HR, payroll, receivables, and more – are also in the cloud, and you’re prepared to decommission your entire local infrastructure.
This is also the case whether you’re using Microsoft Entra ID or another third-party directory, single sign-on, or multifactor authorization provider.
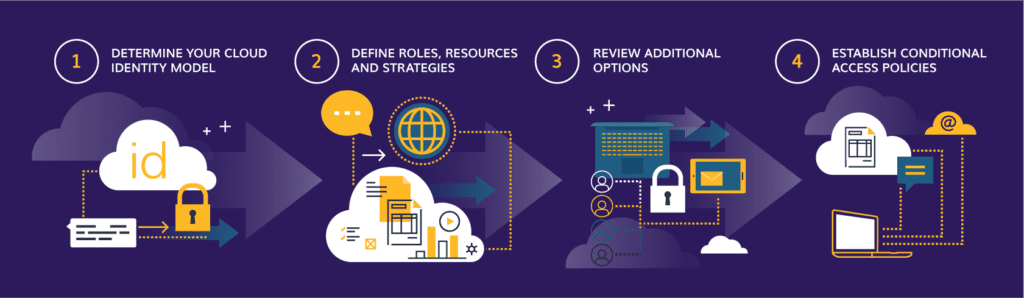
1. Determine your cloud identity model.
If you already have infrastructure available for identity management, check to see if you can federate that with Microsoft 365 and Azure. It’s a simple process, even if you need to synchronize a .local domain. In this case, you will manage your accounts on-premises, including password policies, authentication management, and resource requests.
2. Define roles, resources and strategies.
Determine what applications will be available in the cloud, what roles you’ll use to assign users access to resources, and most importantly, clearly define a group strategy. There are consequences to different types of group creation in Microsoft Entra ID that you should be aware of prior to a migration.
Keep in mind that these decisions don’t take place in a vacuum, and you will need to carefully consider this as a sub-project of your overall cloud migration project.
3. Review additional options.
Take a look at the additional options available to you in the Microsoft Entra ID Premium subscriptions, most importantly ID Protection and Privileged Identity Management:
- ID Protection – risk-based logging and alerts to determine potentially harmful sign-ins, sign-ins from impossible locations, and automated remediation.
- Privileged Identity Management – assign just-in-time (JIT) access to provide a user with elevated access during a specified time window and just-enough-access (JEA) to provide least privileged access to resources.
4. Establish conditional access policies.
In the Entra ID P1 subscription, you’ll find the opportunity to create conditional access policies. If you don’t already have a second-factor authentication provider and policy in place, I recommend exploring the use of conditional access policies to enforce MFA and for a variety of other reasons, especially with the use of mobile devices and your Windows 11 infrastructure.
Once you’ve established who will have access to what, you need to make sure you have security policies in place so that each person knows how to treat your company’s data and keep your organization safe.
4. Security Policies in Microsoft 365
Let’s first make a distinction between the types of policies you have to work with when establishing digital asset protection.
First, there are policies in Microsoft 365 and Azure such as passwords, DLP, labels, Threat management, data governance, and mobile device management. These are the policies you can create in your Microsoft 365 and Azure tenants, and they consist of settings that were likely decided upon in your security requirements meetings. These should be part of your baseline platform documentation already.
There are, however, other policies that you’ll need, and they’re vital to your organization’s operations. These are documented policies that cannot change without your governance board or boards’ approval.
Identity Policy
This type of policy covers items that protect your users, their personal information, and access to your systems.
- Passwords – It’s likely your company manages your password policies on-premises and not in the cloud, but make sure these are documented and updated. NIST’s guidelines can help.
- Multifactor Authentication – Due to NIST’s guidelines, you will want to enforce this for all admins and all mobile or off-network logins.
- Data Loss Prevention – Automatically label documents and emails containing social security numbers or credit cards, and prevent them from being shared outside the organization.
- Mobile Devices – Use some type of device management to govern what devices can connect to your tenant, what apps they can use, and what users can do with those apps.
- Administration and Support – Use roles to determine who will administer what portions of your tenant and when they will have access.
- Onboarding and Offboarding – Be sure to document your process and make concessions for data handling when users leave, especially in a hybrid environment.
Information Policy
This type of policy governs the ingress and egress of your company’s data.
- External Sharing – Document who can share, what they can share, where they can share from, and how to monitor sharing.
- Classification and Encryption – Use IP to allow users to classify, automatically classify, and encrypt information in your tenant.
- Retention – Manage the lifecycle of your data and determine when or if it can be deleted so you retain critical data.
Governance Policy
This type of policy will help you maintain control over the permissions your users have to use your systems.
- Exchange – Document what services your company allows, who can use them, and how to effectively monitor and adjust as needed.
- Teams – Decide on a Group and Team creation strategy, as well as retention plans, external application use, and external sharing.
- SharePoint – Determine strategies for storage management and usage, site creation and lifecycle management, and sharing.
- OneDrive for Business – Decide on quotas and sharing strategy.
- Viva Engage – Determine how you want to use Yammer, and how sharing and group creation will take place.
- Power Automate, Power Apps, Power BI, Dynamics, Planner, Sway, Forms, and more – These are apps that don’t have the traditional Microsoft 365 Admin Center. But don’t let down your guard. They still have access, usage, and sharing policies that you need to govern.
- Microsoft 365 Groups – You’ll need a naming strategy and retention policy, ownership and membership policy, and an external sharing plan. Remember that these are the underlying organizational units for Teams, Planner, Power BI, and more.
In many cases, you’ll find that your existing policies will work fine and will only need to be tweaked a little. Many of these applications and processes, however, won’t have well-defined policies in place, and you will need to document and manage them.
To manage and maintain all of this, however, you need to understand how your own physical servers and Microsoft’s physical architecture work together to protect your company’s data.
5. Physical Architecture: Security Features
Microsoft’s physical architecture uses the same principles most organizations use to secure a data center. Because of the nature of Microsoft data centers and the information kept in them, securing the physical infrastructure is as paramount as data availability.
Some of the physical protection features in use by Microsoft’s data centers are:
- High-security perimeter fences.
- 24/7/365 surveillance.
- Vehicle checkpoints.
- World-class access procedures to facilities.
- Multi-factor, biometric entry points.
- Full body metal detection.
- On-site hard drive destruction (shredding).
- State-of-the-art fire suppression.
- Secure access to physical components.
- Geo-located and geo-replicated data.
You are likely using many of the security features and principles listed above where they make sense in your own organizations. That’s good.
The question is, how will you architect your network for the change? That depends on your final goal.
- Will you peacefully coexist?
- Are you going to extend your directory to the cloud?
- Do you want an isolated tunnel between your location and Office 365?
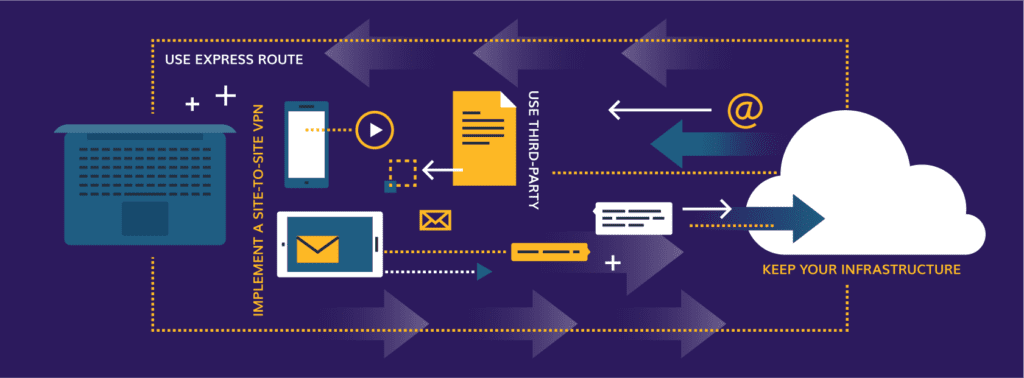
Option 1: Keep Your Infrastructure
This one is really simple. You keep your infrastructure in place and allow the URLs and IP addresses required for Microsoft 365 through your firewall(s).
This uses your current ISP and the public internet in the same way your users access it today. Traffic is encrypted and flows through a secure channel. Microsoft 365 and Dynamics 365 are designed for this type of access.
Option 2: Use Express Route
In certain situations, we recommend ExpressRoute. You still keep your infrastructure in place, but this is a private connection between your infrastructure and Microsoft’s data center through an ExpressRoute carrier, widely available in the U.S.
This type of connection offers higher security, reliability and speed with lower latencies than internet connections. Pairing these connections with other regions requires an add-on but ensures your routing remains optimal for performance.
Option 3: Implement a Site-to-Site VPN
If you’re planning to use an Azure infrastructure workload like a virtual network or you plan to extend or replace your Entra ID entirely, then you have a few options.
You can use the ExpressRoute solution as we discussed in Option 2, or you can connect your on-premises routers to an Azure Gateway using a site-to-site VPN. The gateway can then provide customized access to resources with user-defined routing.
Option 4: Opt for a Third-Party
If you’re in between a site-to-site VPN and ExpressRoute, there are plenty of third-party network appliances in the Azure marketplace that can provide faster than site-to-site VPN with secure routing between your routers and an Azure Gateway. These devices sit between options 2 and 3 above. Barracuda and Cisco are popular device providers you can check out.
This is in no way a comprehensive look at the infrastructure configurations possible. Rather, it’s a broad overview to help you start planning.
There are plenty of considerations based on workload, size and directory structure that can either add complexity or simplify the above approaches.
6. Business Continuity and Disaster Recovery in Microsoft 365
Once you’re fully set up in your hybrid or cloud environment, you need to implement a few additional policies and procedures, the most important of which is a business continuity and disaster recovery plan.
But what is your organization ultimately responsible for versus Microsoft’s role as your provider? You have plenty of options to make sure your data is protected in a worst-case scenario.
Microsoft’s Responsibilities
Microsoft remains committed to transparency when it comes to service health monitoring and outage notifications and updates. They have also implemented a system of geo-redundancy that makes it extremely unlikely for a complete Microsoft service outage to happen across all data centers and all services.
The company ensures that customer data is available whenever it is needed through the following features:
- Data storage and redundancy: Customer data is stored in a redundant environment with robust data protection capabilities to enable availability, business continuity, and rapid recovery. Multiple levels of data redundancy are implemented, ranging from redundant disks to guard against local disk failure to continuous, full data replication to a geographically diverse data center.
- Data monitoring: Microsoft 365 services maintain high levels of performance by:
- Monitoring databases:
- Blocked processes.
- Packet loss.
- Queued processes.
- Query latency.
- Completing preventative maintenance: Preventative maintenance includes database consistency checks, periodic data compression, and error log reviews.
- Monitoring databases:
Administration Responsibilities
It’s up to us as the customer, however, to ensure we are aware of the level of service we can expect and monitor the availability of our own tenants. Here are some basics for Microsoft 365:
Exchange:
- By default, the recoverable item store is set to keep deleted items for only 14 days.
- You can increase this 14-day value, but it can only be set to a maximum of 30 days.
- All Microsoft 365 licensing plans have a soft limit of 20GB of recoverable items storage per user, at which point users will receive a warning, and a hard limit of 30GB, at which point the system will delete the oldest emails first. However, individuals can configure their mailboxes with different quotas.
- The litigation hold version of the recoverable items store has no size or version limits.
SharePoint and OneDrive:
- Deleted items remain in the Recycle Bin for 93 days unless the recycle bin storage exceeds its quota.
- SharePoint Online data is backed up every 12 hours.
- Backups are kept for an additional 14 days.
- One-hour recovery point objective (RPO): Microsoft maintains a copy of your SharePoint Online data, ensuring it is less than or equal to one hour old.
- Six-hour recovery time objective (RTO): If a disaster knocks out or disrupts a hosting data center, Microsoft tries to ensure that organizations can resume service within six hours after the disruption.
Users have a tremendous amount of control over the deletion and restoration of their own personal documents. Administrators have at least 30 days to retrieve data from their tenant as data is first soft deleted.
Did a user account get deleted accidentally? No problem: Recreate it, synchronize it, and access the data. Of course, the two-stage recycle bin in SharePoint has been around for a while now, so no problem there, either.
OneDrive users have a point-in-time restore utility built-in, so be sure users are aware of the feature.
Data Retention in Office 365
Don’t forget about retention policies for data across Microsoft 365. These policies can ensure you remain legally compliant with any industry regulations you might have. Managing these policies typically requires two actions:
- Retaining content so it can’t be permanently deleted before the end of the retention period.
- Deleting content permanently at the end of the retention period.
With a retention policy, you can:
- Decide proactively whether to retain content, delete content, or both – retain and then delete the content.
- Apply a single policy to the entire organization or only specific locations or users.
- Apply a policy to all content or just content meeting certain conditions, such as content containing specific keywords or specific types of sensitive information.
Additional Business Continuity Tips
Beyond maintaining business continuity on your own using Microsoft 365’s procedures, there are a couple of other things you can do to keep your data safe:
Use Outside Help
If you’re interested in defining and managing what you keep, where you keep it, and how often you gather it, you also have a few options:
- See if a hybrid or scripted solution would work.
- Use a third-party SaaS solution to fill this gap.
Explore Azure Cloud Security Options:
There are a few additional options from Azure Cloud security to help you maintain your data integrity:
- Failover your on-premises environment to Azure if you can’t move it all yet.
- Use Azure’s site recovery.
- Use an Azure partner for disaster recovery.
You won’t find 20-plus-year-old strategies anymore for a continuity and disaster recovery scenario. Today, it’s more convenient, cost-effective, and simpler to find continuity and disaster recovery as a service.
Beyond disaster recovery, there are a few other operations you need to have in place to support digital asset protection in Microsoft 365.
7. Operational Support Structure for Digital Asset Protection
If you’re a large enough organization, you are likely transitioning teams from their on-premises duties to new cloud responsibilities. We typically recommend your support team is .2 percent of the organization’s supported community, so two support people for every 1,000 users.
When we work with clients to plan, rollout or remediate Microsoft 365, we look at the entire IT structure, the number of users, what workloads are being rolled out, and how current support structures can be modified for the cloud.
Your first-level help desk will be key in taking some of the repetitive tasks away from your admins, and an updated knowledge base will provide a reference to help them.
If you are the help desk and the global admin, keep a knowledge base for yourself in a SharePoint list for easy reference.
Service Availability Monitoring
It’s up to us to ensure we are aware of the level of service we can expect and that we monitor the availability of our own tenants.
If a service falls below the SLA documented by Microsoft, you will need proof of that outage. Keep an eye on the service health dashboard in the admin center.
You can find service incidents in your Microsoft 365 Admin Portal, and those come in two varieties:
- Planned maintenance events: Planned maintenance is regular service updates from Microsoft done to infrastructure and software applications. Notifications about planned maintenance events let customers know about service work that might affect their service from Microsoft. Customers are notified no later than five days before all planned maintenance through the message center in the admin portal. Microsoft typically plans maintenance for times when service usage is at its lowest based on regional time zones.
- Unplanned downtime: Unplanned service incidents happen when one of the services in the Microsoft 365 suite is unexpectedly down or unavailable.
Monitor the message center at least weekly, if not more often, for updated change notifications, any actions required, and expected outages. Microsoft Defender has default alert policies configured to send admins email messages in a variety of circumstances, such as:
- A mail flow rule has been created.
- Malware is detected.
- An unusual volume of email has been detected.
- Unusual external user activities have been detected.
- And more.
The Secure Score dashboard is a good place to start for a visual look at anomalies and for tips on what to update next. Beyond Secure Score, you can also use the following to monitor service availability:
- Microsoft 365 Admin App.
- Add-in for Microsoft 365 for System Center.
- The service communication API.
- Third-party provider of monitoring solutions.
Enhancing Monitoring and Supportability
If you are interested in enhancing out-of-the-box security monitoring, check out Microsoft Defender for Cloud Apps. This gives you further insight into activity, app use, alerts, and log reviews, among other tasks. It allows you to create policies, from templates or from scratch, that give you deeper insight into shadow IT, allowing you to better control where you store sensitive information.
Another security enhancement is Microsoft Entra ID Protection. Entra ID Protection is a collection of algorithms that determine if a user sign-in is risky or not. If you’re already using conditional access, you can set up the tool to deny access if Azure determines the sign-in to be of a risky nature. This will take some testing, but you can at least determine if the sign-ins are coming from unknown IP ranges (those not associated with a country) or if the sign-ins involve impossible travel (for example, you can’t sign in from an IP address in London and five minutes later sign in from a different IP address in New York).
These monitoring and operations tasks usually take a few months to settle into your organization’s work pace, so be attentive and flexible early on. You should quickly find repetitive tasks that you can manage and automate more effectively using PowerShell or other third-party add-ins.
Almost anything you can do with the UI, you can customize and do it through PowerShell. If the built-in reports don’t offer the data to meet the needs of a specific report request, the information is usually available from the output of a script. You must be a global admin to use PowerShell with Microsoft 365.
Digital Asset Protection in Microsoft 365: Final Thoughts
While the cloud offers undeniable benefits for collaboration and scalability, protecting your organization’s digital assets remains paramount, whether your organization chooses a hybrid approach or fully adopts the cloud.
We’ve explored the various facets of digital asset protection within Microsoft 365, highlighting the importance of a holistic approach that covers everything from encryption and identity control to compliance, policies and business continuity.
By embracing a comprehensive approach that incorporates these key elements, you can ensure the security of your digital assets in Microsoft 365, empowering your organization to use the cloud’s full potential with peace of mind.
Do you want to fully tap into all Microsoft 365 has to offer? Our Modern Workplace experts can guide you through best practices to make your collaboration efforts seamless. Talk to an expert