In this multi-part blog series for Identity and Access Management (IAM), we take a look at IAM capabilities, complexity and challenges organizations face today. We also address why assessing your IAM environment is more critical now than ever before.
Identity and Access Management Series Part 3
In this part of our Identity and Access Management (IAM), we explore different design and configuration options for hybrid identity using Microsoft solutions. We will try to answer what factors add to the complexity of IAM solutions for your organization.
Microsoft Hybrid Identity Stack
To show how a modern IAM implementation for any organization looks, we discussed Microsoft’s identity components that span on-premise and cloud-based capabilities. Active Directory Federation Service (ADFS on-premise) and Microsoft Azure AD (Cloud) are two identity providers from Microsoft which provide authentication mechanism to applications.
Microsoft Azure Active Directory is a modern identity management system spanning cloud and on-premise, providing a common control plane to manage your identities, credentials, devices, applications, and accesses to them. It provides capabilities like synchronization with on-premise directories, SSO to thousands of SaaS applications, machine learning-based security and usage reports, alerting, multi-factor authentication, company branding, self-service password reset, group management delegation, an enterprise-scale service level agreement (SLA), and more which will help provide the level of reliability required by enterprises with advanced needs in identity and access management.
The diagram below provides the modern identity landscape. Our intention with this diagram is to visualize the complexity of IAM. The arrows represent the digital identity flow in the form of the federation and claim-based identity, which we discussed in our second blog.
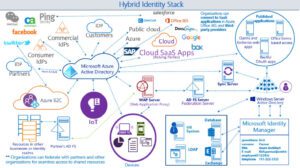
The rapid increase in usage, number of consumer devices, and universal information access are changing the way people perceive technology and also how technology shapes their personal and work lives. The constant use of technology throughout the day, along with easy access to information, is exceeding the traditional boundaries we discussed in the first blog of this series.
Accommodating the consumerization of IT presents a variety of challenges. Conventionally, organizations owned and managed most or all devices their employees use in the workplace. Policies and processes focus on device management and are usually on a relatively small, tightly controlled and managed set of corporate-approved hardware subject to predetermined corporate replacement cycles.
The diagram above shows the challenge regarding complexity, which brings us to the question: What is the correct way of dealing with this complex IAM challenge?
What Adds Complexity to IAM?
Consumer-based devices proliferation
From an IAM perspective, the number of users for which organizations need to provide secure access continues to increase exponentially, whether they are employees (B2E), other businesses (B2B), or direct customers or consumers (B2C). Users can be internal or external, and they are bringing with them a broad cross-section of devices with a variety of authentication requirements and options.
Company mergers and acquisitions activity
Many organizations continue to grow through mergers and acquisitions, and IAM teams must deal with more than a single province of identities for all applications. This issue poses a significant challenge when trying to secure an identity solution.
Different identity accessing different applications
Identity providers today have identities of employees, non-employees, partners, vendors, and consumers—all needing to access resources (applications). We cannot get away with merely securing on-premise identity stores and shoving both enterprise entities and consumers into one place.
Partner identities bring risk. What happens if the partner’s worker leaves and goes to a competitor? Will the company revoke provided access in time, or will they still have back-door access through an untracked application? Customer and consumer volumes bring access management needs that are orders of magnitude greater than just managing employee access. The scale is entirely different, and the business implications and regulatory requirements increase the complexity of seamless and secure access. IAM capabilities will make sure we meet the goal and still improve customer experience.
Meeting complex regulations
Many applications, particularly consumer-based ones, must follow the GDPR. Every organization must allow individuals to consent to the storing of personal data in compliance with GDPR. Personal individual data relates to anything that identifies a person, and which needs specific compliance for the processing and control of the data and how it is shared. Everyone company that holds and processes personal or individual data must implement GDPR.
Any company failing to comply with the GDPR can incur a monetary penalty to the company processing or holding the personal data. GDPR gives rights to people (known in the regulation as data subjects) to manage the personal data that has been collected by an employer or other types of agency or organization, known as the data controller.
The GDPR gives data subjects specific rights to their data; these rights include obtaining copies of it, requesting changes to it, restricting the processing of it, deleting it, or receiving it in an electronic format so it can move to another controller. A formal request by a data subject to a controller to take action on their personal data is called a Data Subject Request or DSR. Regulations like these are pushing organizations’ current legacy IAM solutions beyond their capabilities for better privacy control at both the device and Identity levels.
Data everywhere
When it comes to customer data, it becomes a challenge for organizations to have a single view of the customer or to link customer or consumer data across business units and data silos. However, doing so is critical to securing customer and consumer data and ensuring compliance with industry and governmental regulations.
How are you protecting sensitive data? What are your practices and processes for registering the applications to IDP, granting and maintaining an entity’s profile, getting consent, and applicable access? Who has access to what data? The answer to these issues requires a thoughtful and well-designed approach to an IAM project.
Identity Strategy
Hybrid environments without an identity strategy can create challenges. The complexity of managing identity and access across users, apps, and devices is compounded by the enormous growth in the number of endpoints, the accelerating rate of attacks from a variety of vectors, and increasingly complex operations of securing and managing identity access across and beyond the organization simplifying a complex and chaotic identity environment is not only ideal, but it’s also attainable—through these four steps:
- Move employees to a single identity to improve productivity
- Reduce management overhead through simpler identity infrastructure
- Monitor anomalous activity for greater security
- Give users the tools to be secure.
In Conclusion
As the organization finds itself working across on-premises and cloud environments, managing identity, how employees access services, and how IT governs this access can become complicated. In our final blog of the series, we will discuss how to handle this complexity in any organization.

