Cyber threats continue to evolve, and delaying action increases the risk of financial and reputational damage. A cybersecurity maturity assessment helps businesses strengthen their defenses before an attack occurs.
Cyberattacks are increasing in frequency, and they’re more expensive than ever when it comes to financial loss and reputational damage. Attackers are using sophisticated techniques like ransomware-as-a-service (RaaS), phishing powered by artificial intelligence (AI), and zero-day exploits. Ransomware alone is set to cost businesses $265 billion annually by 2031.
You can strengthen your business’s defenses before an attack occurs with proactive tools like a cybersecurity maturity assessment, or CMA. CMAs help identify vulnerabilities, assess your readiness, and build a structured cybersecurity road map for improvement and long-term protection.
What Is a Cybersecurity Maturity Assessment?
A CMA is a structured evaluation that measures how an organization prevents, detects, and responds to cyberthreats. Staying proactive and ahead of the curve is crucial in cybersecurity, and modern businesses need to go beyond basic compliance to assess real-world security readiness.
Cyber maturity refers to an organization’s capability to protect against, respond to, and recover from cyberthreats through the assessment of its processes, policies, technologies, people, and governance structures.
A cyber resilience maturity assessment also uses standard frameworks like NIST, CIS Critical Security Controls, ISO 27001, and CMMC as benchmarks to help organizations move from reactive to proactive security.
Comparing In-House CMAs vs. Third-Party CMAs
Depending on budget and internal resources, a CMA is performed by in-house security or cybersecurity professionals, or it’s outsourced to a third-party consulting firm. Businesses can also take a hybrid approach with in-house teams combining their knowledge with the specialized expertise of an outside vendor.
For businesses with a limited budget, an in-house CMA might suffice if internal teams have the knowledge, skills, and tools to commit to a thorough review.
For the most unbiased and comprehensive approach, you can use a third-party consulting firm that offers specialized access to expertise and tools, industry benchmarking against competitors, and external validation for compliance and regulatory audits.
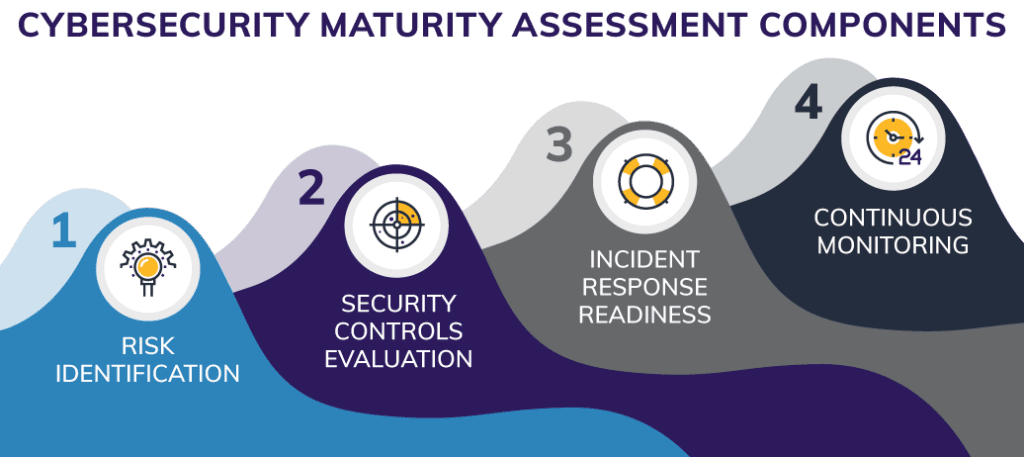
Components of a Cybersecurity Maturity Assessment
A thorough CMA involves four crucial phases that test every aspect of an organization’s security posture. It also provides both short-term and long-term recommendations and guidance for your business.
Here are the four components of a CMA.
1. Risk Identification
The first phase of a CMA aims to identify security weaknesses and potential threats. This might involve a mix of human checking, automated scans, or third-party penetration testing to identify risks.
It also involves:
- Manual code reviews and security audits to identify weaknesses
- Vulnerability scans to detect misconfigurations or outdated software
2. Security Controls Evaluation
Then, the assessment should purposefully stress firewalls, endpoint security, access controls, and other defenses to check for vulnerabilities and gaps. This happens through penetration testing, real-world simulation, vulnerability scans, or incident response readiness testing.
It also involves:
- Red team exercises to mimic real-world hacking simulations
- Endpoint response testing through more simulated attacks and response readiness testing
3. Incident Response Readiness
Experts performing the CMA should also assess the organization’s ability to detect, contain, and recover from an attack, including how quickly an organization detects a threat and isolates the affected systems.
This also involves:
- Security information and event management (SIEM) review to see if alerts properly trigger
- Automated endpoint threat detection to verify if the system detects and stops the intrusion
4. Continuous Monitoring
The final phase of a CMA ensures that security programs evolve with emerging threats through proactive security testing and regulatory alignment.
It also involves:
- Other automated, real-time continuous monitoring from endpoint detection response systems, network traffic analysis, and always-on firewalls
Now that you’re confident about the phases of an ideal CMA, let’s discuss the best time to get a cybersecurity assessment.
When Is a Good Time to Get a Cyber Maturity Assessment?
Cyber IT maturity assessments are helpful at these crucial checkpoints:
After a Security Incident
If the worst does happen, and your organization experiences a data breach or cyberattack, a CMA helps assess damage, identify gaps, and strengthen defenses. A CMA involves incident analysis and incident response evaluation, and it can provide recommendations on better employee training or continuous monitoring tools.
Before a Compliance Audit
A CMA prior to a compliance audit helps your business maintain industry standards and prepares critical documentation for compliance.
For example, a healthcare provider preparing for a HIPAA audit could double-check their protocols align with HIPAA’s regulatory requirements and find gaps before investigation.
During Rapid Growth or Mergers
When companies experience rapid growth, they’re constantly adding new platforms, vendors, and employees, potentially leading to gaps in security. Also, company mergers can rapidly expand infrastructure, and newly integrated platforms might cause security risks.
For example, Centric Consulting worked with an acquisition team to integrate and consolidate technologies, platforms, and resources while enhancing security throughout the integrations.
When Security Is Unclear
Cybersecurity is an important line item in a business’s IT budget, but if existing tools and policies are not being used, this money is being wasted. A CMA can identify if existing protocols are being followed and are effective.
Before Investing in Security
Cybersecurity is an expensive investment, and a CMA helps efficiently prioritize and allocate resources and budget by identifying the most critical vulnerabilities. Instead of investing in different tools or protocols here and there, a CMA creates a well-defined road map that prioritizes needs based on budget and resources.
No matter what exact phase your business is at, all organizations benefit from cybersecurity maturity assessments.
Why Your Organization Needs a Cybersecurity Maturity Assessment
Whether your business is growing quickly, is experiencing a merger, or just went through a data breach, a cybersecurity maturity assessment identifies crucial gaps and can prepare your business for the long term.
Plus, if your organization isn’t fully using tools and resources, a CMA identifies potential wasted money.
Here are other benefits to a CMA:
Proactive Security, Not Just Compliance
Modern-day cybersecurity goes beyond basic compliance, especially as threats and attackers quickly become more sophisticated. CMAs uncover hidden vulnerabilities that basic compliance audits might overlook.
Cost-Effective Risk Management
Effective cybersecurity isn’t cheap, but it helps prevent an even more costly data breach. A CMA can identify your biggest risks so your team can efficiently allocate a limited budget to the most important aspects. Global risk management spending is set to hit $210 billion in 2024 and could exceed $310 billion by 2028, so it’s a huge portion of current and future IT spending.
A Clear Cybersecurity Road Map
While most leaders claim cybersecurity is of utmost importance, many lack a long-term, well-defined road map and program. A CMA can offer data-driven recommendations for short-term vulnerabilities as well as a long-term plan for more proactive, sophisticated protection and risk management.
Stronger Security and Compliance
Noncompliance with regulatory frameworks can have devastating effects. A CMA strengthens cyber defenses, reduces legal and regulatory risks, and enhances overall compliance with frameworks like NIST, CIS Critical Security Controls, and ISO 27001.
CMAs provide a clear cybersecurity road map and cost-effective risk management recommendations, and they create a cyber maturity assessment framework for proactive security beyond compliance. Here’s how to choose the right cybersecurity partner for this crucial proactive assessment.
How to Choose the Right Partner for Your Cybersecurity Assessment
Look for companies with industry-specific experience, such as healthcare, financial, retail, or government, to ensure they have deep experience and familiarity with regulatory frameworks relevant to your business. Confirm they have successful past work or case studies in your industry. Emphasize process over product.
The most valuable assessments focus on the collaborative journey to creating a tailored final report. Prioritize partners who demonstrate commitment to understanding your unique challenges and working alongside your team throughout the entire assessment process.
Ensure your cybersecurity partner adheres to established frameworks such as NIST, CIS, ISO 27001, and CMMC and does more than provide lengthy reports. Determining the appropriate next action is important through a CMA so leadership and IT teams don’t get bogged down with tons of information and data. Work with a provider that supports long-term security resilience instead of providing steps for one-time assessments.
To ensure your ideal provider is thorough, comprehensive, and cost-effective for your needs, make sure your provider:
- Has deep industry experience backed by testimonials and customer success stories
- Covers threat detection, incident response, and recovery
- Provides both short-term fixes and long-term strategic cybersecurity development
- Offers tools and recommendations for vendors and providers
- Displays transparent pricing and fees for all recommendations
- Helps support long-term compliance and risk management
No matter your business phase or goals, a CMA provides a road map for your business to assess existing cybersecurity protocols and ensure your business is creating a competitive advantage for years to come.
Whether your business is acquiring another, you lack insight into protocols being used, or you just experienced a cyber incident, contact Centric Consulting to discuss a CMA for your business that includes actionable solutions.
You know you need to protect your brand and financial stability by prioritizing cybersecurity. But do you know where to start? Our Cybersecurity team is ready to help you focus on everything from strategy development to penetration testing.