We walk through using git pre-commit hooks in your git workflow to supercharge your software development lifecycle.
Using git pre-commit hooks in your software delivery pipeline helps achieve better quality software with faster time to market. Developers have more access to define additional aspects around the infrastructure needed to run their applications. It is critical to lower the risk of changes completed in development to supply additional confidence and increase velocity.
This is because implementing git pre-commit hooks is essentially executing local scripts to check for certain quality and policy items prior to pushing the commit. This is one less step you would normally do manually. The number of available checks is extensive and covers multiple programming languages. This simple addition to a Continuous Integration/Continuous Development (CI/CD) pipeline is one way you can take steps towards “shifting left” with security.
In this blog, we will talk more about how using git pre-commit hooks is one of the best practices in modern software development lifecycles (SDLC). We will also discuss what it means to “shift left” as it applies to committing important files that may expose surface area or otherwise goes against policy.
Git Pre-commit Hooks, Defined
Using git pre-commit hooks is comparable to using linting tools whose purpose is to check for correct syntax and formatting. The tool itself is a set of scripts that are kept along with the git information that is local to your PC. You can use them on multiple languages existing in the same repository. Its design allows for managing the installation and execution of the various hooks available without root access and on an as-needed basis.
While this is very much something that aids in code reviews, it is also an initial part of an end-to-end solution for automated software delivery. With Infrastructure as Code (IaC), any changes in the infrastructure of a project need to consider the downstream effects. In the case of a Kubernetes manifest, this means ensuring you don’t commit something like private key data to the repository.
Now let’s look at how pre-commit hooks help you shift left.
Why Shifting Left is the Right Direction
Shifting left is a practice getting a lot of attention in the software industry. OWASP stated shifting left is geared towards keeping a pipeline and its resulting artifacts more secure. Take a Kubernetes manifest file, for example. This configuration file can expose various ports or credentials you should not commit to code. You can check these against policy with tools like git pre-commit hooks, similar to how developers use code linting tools.
By shifting left, teams can find and prevent issues much earlier in the SDLC process. This method is useful for finding quality, security and policy issues as early as possible. Enforcing these checks prior to reaching the codebase can prevent developers from using offending code in additional feature branches.
Keeping Things in Check
If a developer is not careful, they may inadvertently create more attack surface area for an application due to modifications done to the manifest file. These files, along with other files that hold settings, control much of the infrastructure or permissions used by an application. In many cases, the negative effects of these changes are not found until further down the line. Sometimes, even after being deployed to a production environment.
This increased ability to have more surface area available for miscellaneous attacks is the drawback of giving those who may not have security at the top of mind more control. Using tools such as git pre-commit hooks allows for a quick pass over these critical configuration files to help with security. Injecting a git pre-commit hook into a development workflow can help surface these issues well before they are deployed to your various environments.
A Look at Git Pre-commit Hooks in Action
Prior to using pre-commit hooks, you should choose one of the methods of installation based on your development environment. In this example, we will look at an application that we will run inside a Kubernetes cluster.
To begin, we will install pre-commit using “pip” with the following command:
$ pip install pre-commit
To verify it was installed, run the following:
$ pre-commit –version
An additional file called .pre-commit-config.yaml will be added to your project by running:
$ pre-commit sample-config > .pre-commit-config.yaml
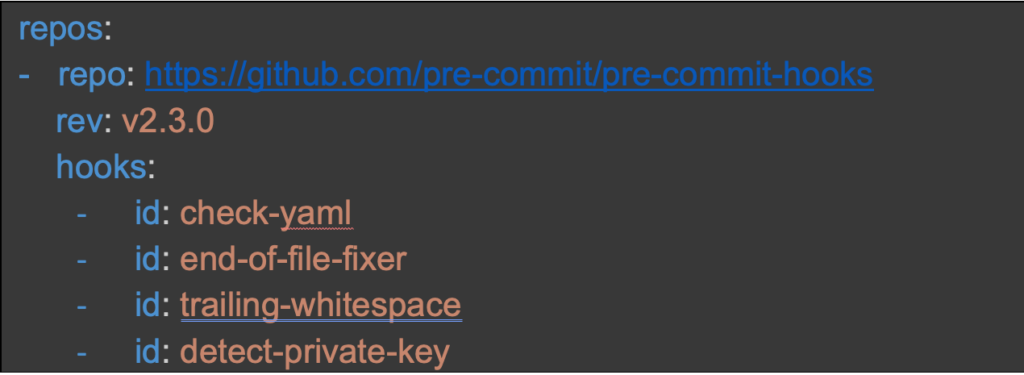
This basic configuration file has examples of commonly used hooks, but we want to ensure we install the hook that checks for the presence of a private key. Open the .pre-commit-config.yaml file and add the hook at the bottom:
Running pre-commit install results in creating the scripts to add the hooks to your project.
$ pre-commit install
Once you complete these steps, a commit results in the pre-commit scripts running without any other actions needed by the developer.
Let us look at an example k8s_manifest.yaml file with a private key we do not want committed to code.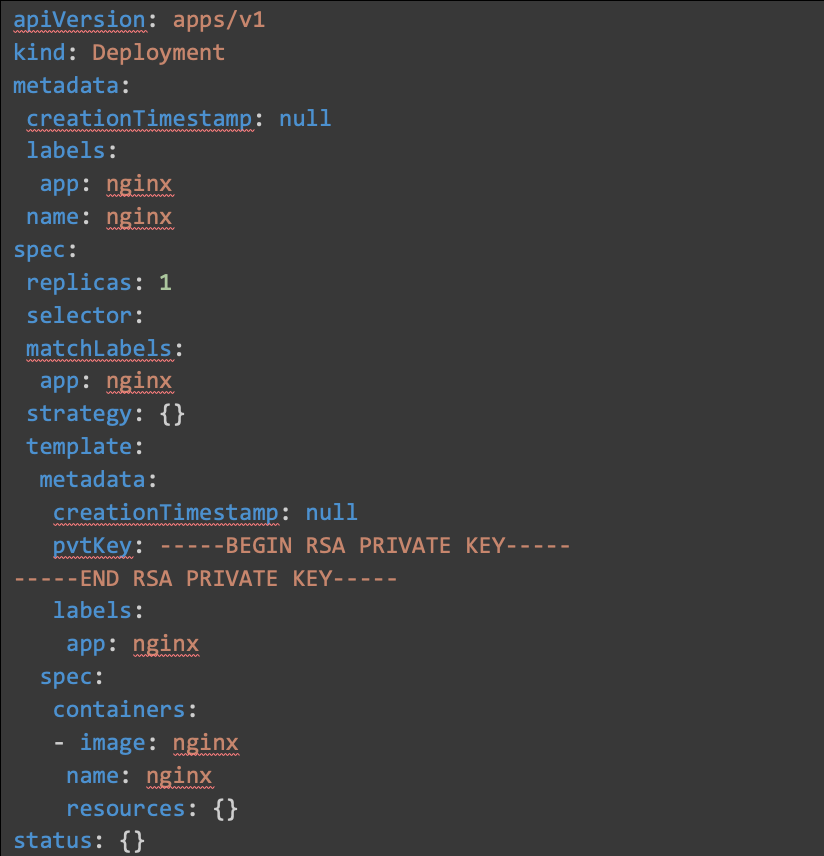
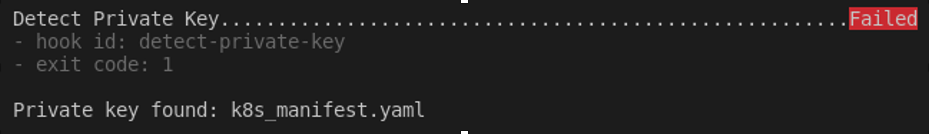
The next command will scan the entire codebase. This ensures all the files are checked against the implemented rules.
In our example, since there is an RSA Private Key inside the manifest, our hook installed for “detect-private-key” will force a non-zero exit code.
$ pre-commit run –all-files -v
Conclusion
Looking at this information, you should see the benefits of using git pre-commit hooks in your SDLC process. This simple step towards shifting left will accelerate the goal of achieving better code quality, security and velocity to help decrease time to market.
Due to their simplicity, savvy teams are using git pre-commit hooks as a quick way to improve their git workflow and supercharge their development.