News of the Colonial Pipeline breach has us all thinking harder about IT security. Read on to learn when you should know, especially if your business is a Microsoft shop.
While analysis of the Colonial Pipeline hack is ongoing, recent reports that an older version of Microsoft Exchange may have played a role is a great reminder to make sure now that all of your software systems are up-to-date.
Microsoft released patches in April 2021 to address the threat, known as HAFNIUM. It targets on-premises versions of Microsoft Exchange 2013, 2016, and 2019. The company’s Exchange Team Blog described the patches, explained how to install them and provided a helpful FAQ.
In addition, the Microsoft Security Exchange Response Center stated:
“Recent events have shown, security hygiene and patch management are more important than ever as the industry works to protect from both sophisticated and common cybercriminal activity. First and foremost, it is really important that our customers are on the latest version of software which has up-to-date security updates. Microsoft is committed to supporting our customers through this and we urge customers to make every effort to update their software to the latest supported version and install security updates, if automatic updates are not already turned on, as soon as possible to help protect from today’s dynamic threat landscape. It is common for attackers to shift their efforts to exploit recently disclosed vulnerabilities before the latest updates or patches are installed, which is why it is so important that customers migrate to the latest supported software. . . . [W]e recommend customers install the updates as soon as possible to ensure they remain protected from these and other threats.”
As a Microsoft Gold Partner, we stand behind this statement. In addition, we would mention Microsoft specifically created these patches for on-premises (on-prem) versions of Microsoft Exchange 2013, 2016, and 2019.
Note also that even cloud-based email systems may be using a vulnerable on-prem Exchange server for administration purposes. This puts cloud-based systems at risk, too.
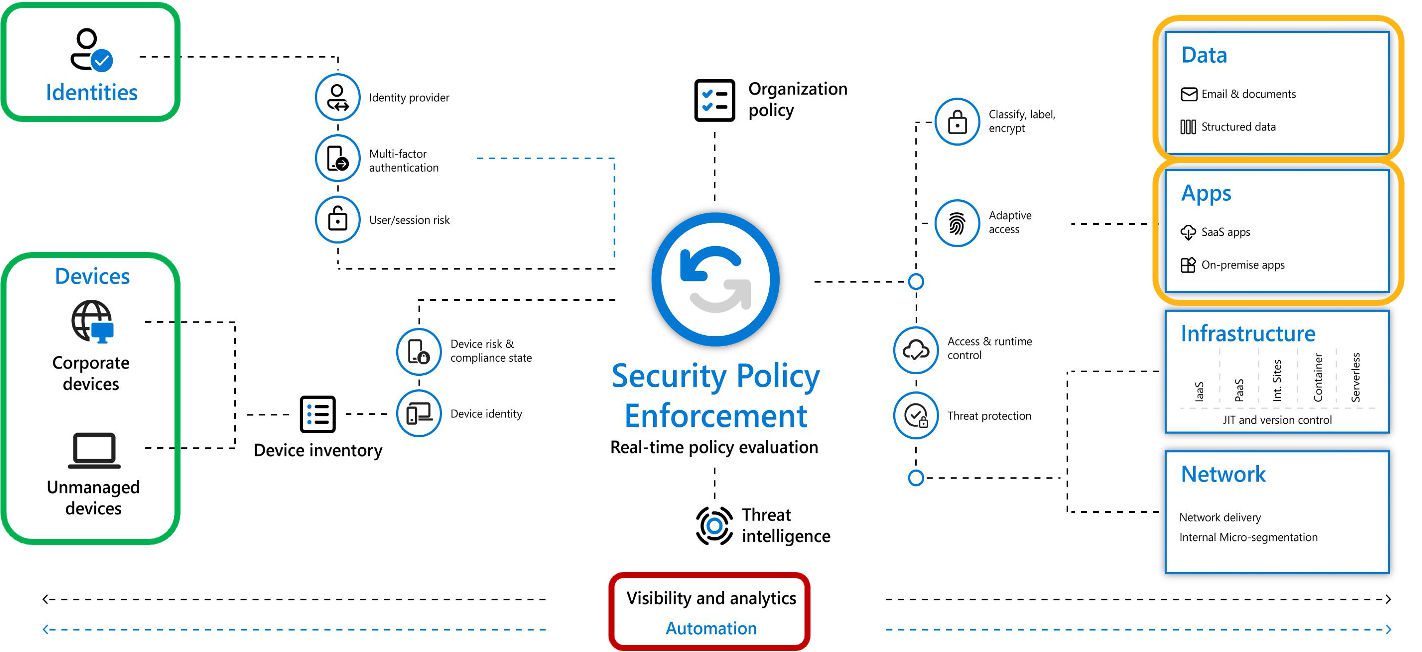
In fact, you should adopt a Zero Trust model and never assume that any system is completely secure, including cloud-based email services like Exchange Online or Microsoft 365 (formerly O365).
To be as safe as possible, we advise our clients to:
- Check now to make sure your software systems are up-to-date.
- Make sure you always enable “automatic updates” on all systems.
- If you have on-prem versions of Microsoft Exchange 2013, 2016, or 2019, install the patches as soon as possible.
- After you install patches, run Microsoft’s script to look for HAFNIUM. Then, run Microsoft Defender or Azure Sentinel tools to further detect and mitigate attacks.
Though Defender and Azure Sentinel are both cloud-based, you can run them on on-prem Microsoft Exchange servers—but it may take some work.
Your goal is to protect not just email systems but your surrounding systems, too. You must build a multilayered system to provide the best depth of defense for your critical IT assets.
While you may have proven solutions in place for managing your legacy infrastructure and networks, you may encounter gaps on your journey to the cloud—especially as you provide employees with the ability to work from anywhere.
We have focused our services on those gaps as hybrid workplaces become the new normal. Below is a schematic of our Zero Trust approach: