Regularly testing compliance controls helps you identify security gaps before they lead to breaches. Learn how checkbox compliance fails against modern threats along with practical methods for validating security measures through continuous monitoring and real-world testing scenarios.
You have a list of compliance requirements, so you go through it and check the boxes. All set? No. Merely checking the boxes gives you the illusion of covering all of your bases, but in many cases, it’s merely the beginning. You need a systematic, deep testing system that proactively identifies issues to bolster your compliance. You then use this information to take definitive steps to reduce your compliance risks. But what’s involved in testing your compliance controls, and is it really worth the time?
Let’s dig in to answer these and other common questions about testing compliance control mechanisms.
How Attackers Exploit Compliance Controls
Compliance controls are easy for a crafty attacker to exploit. Often, you may go to long lengths to adhere to compliance standards but neglect a key vulnerability.
For example, suppose you run compliance for a healthcare organization. You go above and beyond to make sure all patient data gets stored properly, use multifactor authentication (MFA) systems across your environment, and have airtight role-based access controls. You’re checking all of the necessary HIPAA boxes.
But one day, you allow a third-party vendor to access patient records for a project. They complete the project, you pay them, and it’s back to business as usual.
However, your HIPAA compliance controls and systems do not incorporate a measure to automatically revoke third-party access once it’s no longer needed.
While your employee satisfaction rates are high, the same can’t be said for the vendor. One day, an angry former employee decides to use their access credentials — the ones that should’ve been revoked — to steal sensitive data and sell it to a hacker.
The breach goes undetected for weeks. When it finally comes to the surface, it’s too late. You get hit with penalties, and the reputational damage extends for many months.
Now, if you had performed a compliance audit to ensure you have implemented the proper regulatory compliance controls, you may not have detected this vulnerability. A well-segmented network and adequate access controls can’t stop an attacker armed with legitimate credentials. This is why it’s important to understand the common weaknesses in compliance controls sooner rather than later.
Common Weaknesses in Compliance Controls
While everyone’s compliance measures are different, here are some weaknesses that impact many organizations:
- Policies don’t address emerging threats. Do your policies address phishing attacks powered by artificial intelligence, insider threats, and zero-day exploits involving brand-new threats that security scanners haven’t profiled?
- Employee training doesn’t include real-world scenarios. Do your employees know how to handle a spear phishing attack? Do executives know how to detect whale phishing? Do they understand how to check whether a website is spoofed or legitimate?
- Access controls are excessively permissive. When someone no longer works at your company, is there a system for revoking their credentials? Do you use MFA for all user accounts? What about role-based access? Are there limits in place to control who can access sensitive areas based on their job duties?
- Incident response plans aren’t tested. Have you tested your incident response plans to see if they can handle persistent attacks? What about lateral network penetration or privilege escalation assaults?
- Compliance testing isn’t ongoing. While it’s good to prepare for audits, do you only give compliance-focused attention when an audit is looming? Your compliance testing should be ongoing.
How to Assess and Test Compliance Controls for Risks
By regularly assessing and testing your controls for risks, you can prevent a long list of compliance issues, especially if you use the following guidelines.
Conduct Security Audits and Gap Assessments
A security audit and gap assessment involves evaluating your security policies and the technologies you use to build your safeguards, assessing their effectiveness, and identifying vulnerabilities.
To do this, you should start with a respected framework, such as NIST, CIS, ISO 27001, or CMMC. These give you a structure around which to architect your assessment.
Then, compare your current practices to the best practices outlined in the frameworks you choose. Perform a side-by-side comparison and document your findings, preferably using an easy-to-read chart.
You can then interview those in charge of your security to see how well they understand their roles and responsibilities.
After collecting all of this data and getting everyone on the same page, it’s time to create an action plan. Here’s how you can structure it:
- Document your findings by outlining ways your security program meets, exceeds, or falls short of what your chosen standard describes. For example, NIST SP 800-53 says an organization should disable or remove inactive accounts after a certain period of time.
- Monitor how well you adhere to compliance requirements over time. Laws change, and so does your infrastructure, so continually monitoring compliance is essential.
- Establish an ongoing compliance reporting system. For example, you can set up a rubric you use to evaluate how well you stick to compliance standards and periodically distribute it to stakeholders.
- Set up remediation protocols to address issues. Your remediation system should consist of a list of team members responsible for fixing compliance problems, timelines for completing their work, and who verifies the quality of their work.
Perform Penetration Testing and Vulnerability Scans
Use real-world attack scenarios to find security issues. You can start with automated tools that scan your systems for vulnerabilities. This is a quick way to discover issues you need to address.
You should also make a list of all of the software you use and check to ensure you’re using the latest version. As an addendum to this step, you may have to double-check the compatibility of the hardware that runs your software. Sometimes, wiping out and replacing an old version of your software can raise issues if the new version isn’t compatible with a computer’s or server’s operating system.
It’s also a good idea to include at least a few social engineering-style attacks, such as phishing, in your penetration testing. This lets you check how ready your employees are to stave off attackers.
Assess Access Controls and Permissions
If you don’t already have access control assessment systems in place, it may take a little time to set them up, but it’s well worth it. To do this, you assess every employee’s access — in-house and remote or hybrid. It’s best to avoid starting with a list of current employees from your HR department. You’re better off using your list of access credentials as a starting point so you can check to see if each person with access still works for your organization.
Once you’ve clarified who has access and deleted unnecessary credentials, you can vet each set of privileges, checking to see if they absolutely need to have the access they do. For instance, someone in HR may not need access to customer payment information, and someone in accounts receivable may not need access to HR’s employee management system.
Evaluate Incident Response Readiness
Your incident response readiness evaluation should unfold a lot like a compliance fire drill. This is when you perform tabletop exercises to see how well your teams react to incidents and whether the steps they take meet your compliance needs.
Often, it’s best to divide those involved into teams, such as Red, Blue, and Purple Teams:
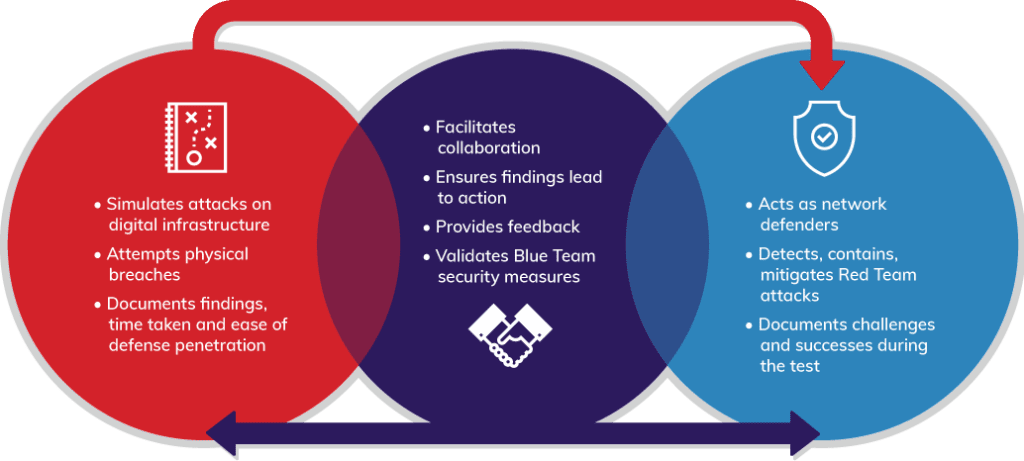
- The Red Team attacks some or all of your digital infrastructure. You may even incorporate physical infrastructure attacks as well, such as an attempt to get into a server room. The Red Team also documents what they find during the attack, highlighting how long it took and the ease with which they were able to penetrate defenses.
- The Blue Team consists of your network defenders. They try to detect, contain, and mitigate the attacks of the Red Team. The Blue Team should also document their findings regarding challenges and successes they experienced during the test.
- The Purple Team ensures collaboration between the Red and Blue Teams and that their work results in actionable analysis. Purple Team members make sure those on the Red Team share their findings with the Blue Team. They also give feedback on the work of the Red and Blue Teams. In addition, the Purple Team validates the effectiveness of the security measures the Blue Team uses to stop the Red Team’s attacks.
Implement Continuous Compliance Monitoring
You can use automated tools, such as security information and event management (SIEM) systems, to monitor your compliance continuously. For instance, some SIEM systems collect and analyze security logs from a range of sources you integrate with them. Others incorporate behavioral analytics, which can detect threats based on how a network segment functions, the speed with which data flows out of your network, or other metrics.
Regardless of the solution you choose, make sure it collects and securely stores logs so you can evaluate them, if necessary, after an incident.
You should also look for features that make it easier to maintain compliance and fight threats, such as:
- Premade compliance templates. Use a template based on frameworks like ISO 27001, PCI DSS, and NIST.
- Automated compliance audit reporting. These are useful when you need to demonstrate compliance to those on your team or external stakeholders you may have to report to.
- Built-in retention policies that conform to compliance requirements. For instance, the Bank Secrecy Act (BSA) requires a company to retain certain records for at least five years. Your SIEM solution can be set up to automatically meet these kinds of storage requirements.
- Real-time threat detection. This flags threats as they occur.
- User behavioral analysis. A SIEM that analyzes user behavior can detect threats based on anomalous user actions, such as logging in from a suspicious location.
- Automated incident response. A SIEM can automatically trigger actions to stop or contain threats, such as quarantining a device or blocking an apparently malicious IP address.
Take Control of Your Compliance Validation System
It’s dangerous to presume compliance, even if you’ve checked all the boxes. With an experienced partner, you can get help testing your security to make sure it defends your network from the most recent threats. Centric Consulting’s compliance experts lean on years of experience to assess if your organization meets the most relevant compliance standards.
[cta bg="purple" button="Get the White Paper" link="https://centricconsulting.com/ub-cybersecurity-critical-importance-critical-infrastructure/"]Cybersecurity for critical infrastructure is vital to everyday life, and it’s up to your organization to help keep it secure. Download our white paper for industry-based tips.[/cta]
Don’t wait for an audit failure or breach — assess your compliance controls today. Contact us











