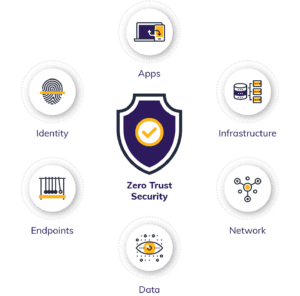
Zero Trust security can keep your business safe from bad actors.
Efforts to enhance employee experience have increased more than ever with the focus on remote work and making it easier to collaborate and improve transactions via digital channels while protecting their data.
These changes have brought to light the importance of establishing a cloud security strategy that keeps their collaboration and transactions in the cloud protected from bad actors without limiting their team’s ability to perform their work.