This comprehensive guide explores the five primary types of access control models — discretionary, mandatory, role-based, attribute-based, and policy-based — and analyzes their strengths, weaknesses, and ideal implementation scenarios.
In brief:
- Different types of access controls offer different types of security and protection.
- Consider your data sensitivity, growth trajectory, and compliance needs when deciding which model or models you need.
- Access controls aren’t something you want to overhaul frequently. Factor in your three-to-five-year growth plans, potential cloud migrations, and emerging technologies like artificial intelligence (AI) when making your decision — because changing later is costly and disruptive.
Access controls are crucial levers within identity and access management (IAM) that determine who sees what and for how long. An incorrect setup means allowing unauthorized individuals into your system. Different types of access controls minimize the risk of insider threats and lateral movement, support zero-trust architectures, improve audit readiness, and build a more seamless user experience by reducing unnecessary friction.
However, modern environments built on cloud and hybrid infrastructure require dynamic and contextually aware access controls. Cybersecurity decision-makers and information technology (IT) leaders must decide which approach best suits their organizational requirements, security posture, and growth trajectory to optimize their security infrastructure while maintaining operational efficiency.
Within the five primary types of access control models — discretionary, mandatory, role-based, attribute-based, and policy-based — you must consider various factors, including strengths, weaknesses, and ideal implementation scenarios.
In this guide, we’ll review the pros and cons of each approach, discuss when to mix and match, and guide you on how to implement them successfully within your organization.
The Different Types of Access Controls
Access controls regulate all permissions. They cover who, what, what actions, when, where, and under what conditions.
In reality, this appears to be a potentially unlimited number of possibilities for each employee and user group within an organization. For example:
- A software engineer can access source code repositories but not client financial information
- A marketing coordinator can view sales records but cannot edit, delete or modify details
- External contractors can only access files between 9 a.m. and 5 p.m. on weekdays
- A sales engineer must use a virtual private network (VPN) on a managed device to perform a live demo
Let’s take a look at five different types of access controls.
1. Discretionary Access Control
Discretionary access control (DAC) restricts resources that individuals own. It’s a flexible model but potentially risky as it’s easy to misconfigure.
For example, a marketing manager might completely control access to a sales presentation but then share it with an external vendor, not realizing it contains proprietary and confidential information. The marketing manager may not fully understand the security implications of sharing this file widely.
Strengths
- Allows users and data owners to define access permissions
- Quick to implement
Weaknesses
- Increases the likelihood of privilege creep
- Lacks centralized oversight from a higher authority
- Potentially exposes sensitive or highly regulated data
- Might violate compliance policies in highly regulated industries
When to Implement
- Ideal for when simplicity and speed matter more than tight control
- Ideal for noncritical systems
2. Mandatory Access Control
Mandatory access control (MAC) establishes fixed, system-enforced rules tied to policies rather than individuals. It’s ideal for the most highly regulated environments in which security policies are nonnegotiable and not open to interpretation. It promotes high security but low flexibility.
For example, within military environments, NIST SP 800 requires mandatory data labeling that directly matches users with a clearance category, such as Confidential, Secret, or Top Secret.
Strengths
- A strong centralized control that leaves little room for human error (almost the opposite of DAC)
- Supports confidentiality and compliance
Weaknesses
- More rigid and more time-consuming to manage
- Might frustrate users with delays or restricted access
When to Implement
- Best for strong, top-down data protection
- Ideal in highly regulated environments and industries such as government or classified systems
3. Role-Based Access Control
Role-based access controls (RBAC) are tied to job roles.
For example, all marketing team members have standard user group access to files, applications and systems, enabling them to complete their daily tasks. Marketing executive leaders and directors may have higher permissions for editing sales data, reviewing confidential financial information, or modifying marketing infrastructure.
Strengths
- Easy to manage at scale due to simplified user grouping
- Creates consistency across departments
- Many industry regulations, like HIPAA and PCI DSS, require role-based access controls
Weaknesses
- Difficult to manage manually
- Lacks contextual awareness
When to Implement
- Ideal in organizations with clear hierarchies
- Fast-growing businesses that are hiring dozens of roles simultaneously
4. Attribute-Based Access Control
A more granular approach to access controls, attribute-based access control (ABAC) is based on user, resource and environmental attributes.
For example, it creates a picture of the department, job function, location, and time to make a dynamic permission decision.
Strengths
- Granular and dynamic
Weaknesses
- Potentially complex and needs oversight and guidance
- Might be overly complex for a simple situation
When to Implement
- Ideal for fine-tuned access within varied conditions
5. Policy-Based Access Control
Policy-based access control (PBAC) is next-generation access control. Its rules are defined by policies that can combine roles, attributes, and context to provide a comprehensive picture that enables intelligent decision-making. It uses high-level business policies to govern access, similar to ABAC, but with a greater focus on specific business logic.
For example, it might be defined that only senior directors can approve expenses over $10,000.
Strengths
- Easy to align with business-level objectives
- Highly scalable with the right tools
Weaknesses
- Requires robust policy documentation and strict governance
- Might become difficult to troubleshoot
When to Implement
- Ideal for scaling businesses that need a mix of flexibility and control
- Best for large enterprise organizations with complex governance or highly regulated industries with strict rules and workflows
Now that you understand these strengths, weaknesses and ideal implementation scenarios, it’s time to choose which access control model fits your organization.
How to Know Which Access Control Model Fits
Choosing the right access control model depends on your users, data and associated risks. It’s a multifaceted decision best made by stakeholders in IT, leadership, and compliance to ensure you’re covering regulatory requirements, long-term organizational goals, and business continuity.
Key considerations include data sensitivity, scalability, workforce diversity and compliance needs.
Assess Your Risk Profile
Carefully consider data classification, confidential information, intellectual property, financial records and more. Consider the following questions to assess your risk profile:
- How sensitive is your data?
- How dynamic are user roles?
- Does your organization need more flexibility or control?
- What is your existing access control policy?
Consider Future Growth Plans
Access controls are a foundational building block for your cybersecurity infrastructure. Ideally, this is not something you’re changing frequently. Emerging frameworks such as zero trust and technologies like artificial intelligence (AI) and machine learning (ML) are rapidly transforming the traditional access control paradigm.
They’re necessitating smarter, more sophisticated, and contextually aware IAM tools that can make intelligent decisions rapidly.
Here are some questions to get you started:
- Is your organization a fast-growing startup or a legacy, traditional brand?
- Do you expect hyper-growth over the next three to five years?
- Are you considering a cloud migration, AI implementation, or other major IT project?
For example, a leading automotive company recognized that their future growth and scalability would suffer without an effective IAM strategy.
To manage high employee turnover and a constantly changing workforce, they employed Centric Consulting to overhaul their approach to IAM. Instead of a segmented, manual process, they received a phased migration rolled out to their team that enforced stronger identity policies without frustrating users.
Measure Integration Readiness
Consider all your current systems, data, user groups, applications and more. Is your infrastructure set up for the model you want to use? Test your current compliance controls before adopting or expanding to a new model.
For example, transitioning from DAC to RBAC necessitates a significant shift in employee behavior, from owning their own access to a standardized, governance-based model. This transition most likely reduces risk and improves consistency, but it’s not without a major shift in behavior. It will require retraining employees, revoking access, granting new permissions, and standardizing across user groups.
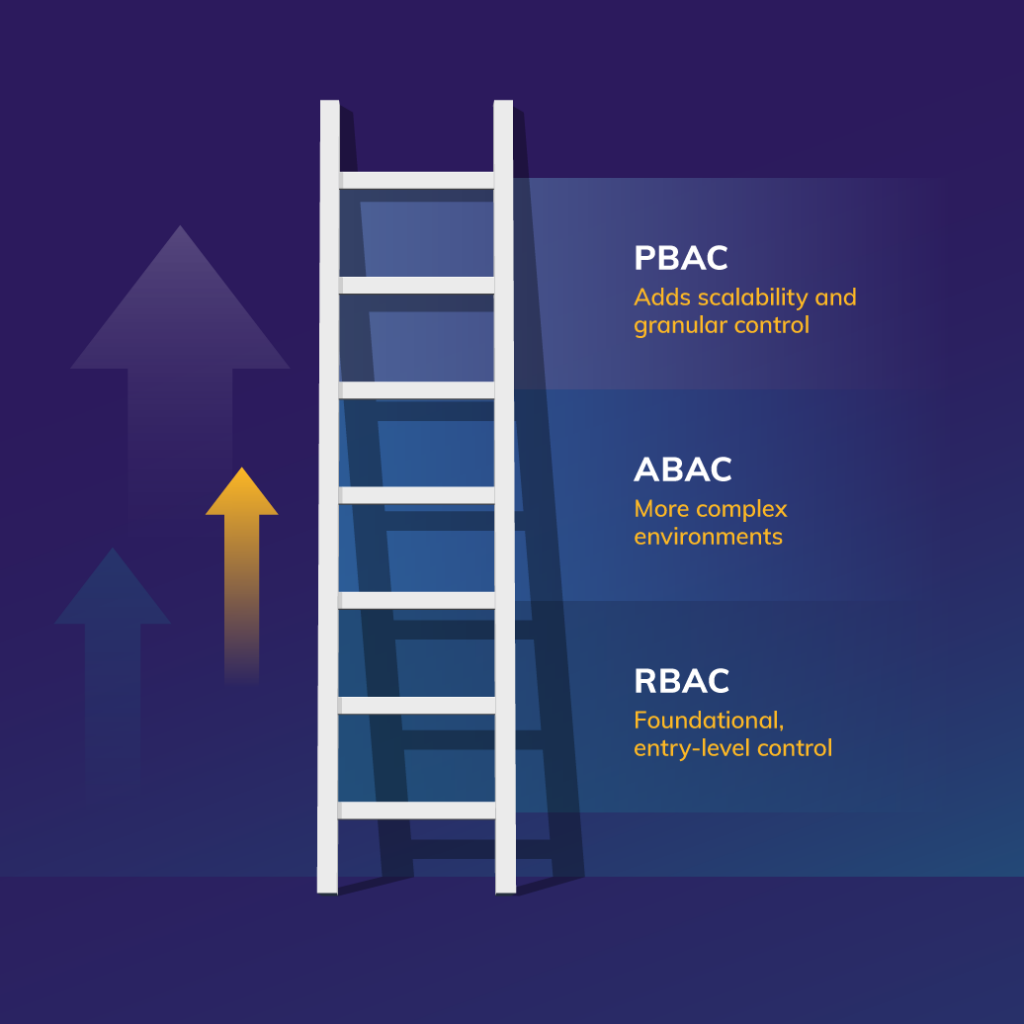
RBAC vs. ABAC vs. PBAC: What’s the Difference?
All these acronyms might start to blend together. For emerging businesses, RBAC is typically the foundational, entry-level control. It’s solely based on job roles and is simple to follow within an organizational structure.
However, as a business grows and environments become more complex, ABAC takes it a step further by adding flexibility with user and environmental attributes.
PBAC takes it even further by applying dynamic, policy-driven rules, which are ideal for organizations that need both scalability and granular control.
Think of it as a ladder where the more complex your environment, the more value you get from moving beyond RBAC.
When to Mix and Match
No single model is perfect, and often, there’s not one right answer for your business. Many organizations blend different models for different use cases.
For example, RBAC is easy to implement and scale with internal employees, while ABAC is ideal for third-party vendors that need oversight and governance. Flexibility with access controls is important, but clarity and the right security measures are more critical.
Use Access Controls for Higher Security
The best access control model is the one that fits your business, not just your tech stack and infrastructure. This crucial IAM decision either enhances your security posture or opens up your organization to vulnerabilities.
Review and refine your access strategy as you grow and layer on additional security such as multifactor authentication, privileged access management, and just-in-time access. Without reducing productivity or frustrating teams, access controls create stronger identity governance within risk-aware situations.
You know you need to protect your brand and financial stability by prioritizing cybersecurity. But do you know where to start? Our Cybersecurity team is ready to help you focus on everything from strategy development to penetration testing. Let’s talk